The Arcive of Official vBulletin Modifications Site.It is not a VB3 engine, just a parsed copy! |
|
|
#1
|
||||
|
||||
|
Code:
http://johnny.ihackstuff.com/index.php?module=prodreviews SEE BELOW (POST # 7 IN THIS THREAD) FOR TOOLS TO HELP COUNTER THESE TYPE OF HACKERS |
|
#2
|
||||
|
||||
|
maybe sending this to the dev's at vb.com would be better>_> so they can plug wholes within the software instead of helping roaming hackers find a good resource to do some hacking on others sites.
|
|
#3
|
||||
|
||||
|
Quote:
KNOWLEDGE IS POWER If the hackers know how to do stuff like that, then website owners should also know what they are capable of, and how to counter it. I don't think that anyone here wants to end up on their page of example sites. EDIT: I changed the link to a URL within code tags, to avoid unlicensed people from seeing the link. Anyone who is licensed will only be interested in protecting their site with this info. |
|
#4
|
|||
|
|||
|
just a note anyone can google that info and come up with a site displaying it
|
|
#5
|
||||
|
||||
|
looking at the queries on google they run, it makes me want to remove my version number from public display
|
|
#6
|
|||
|
|||
|
Quote:
|
|
#7
|
||||
|
||||
|
Here are tools to help with the fight against these type of hackers:
Code:
http://ghh.sourceforge.net/ Code:
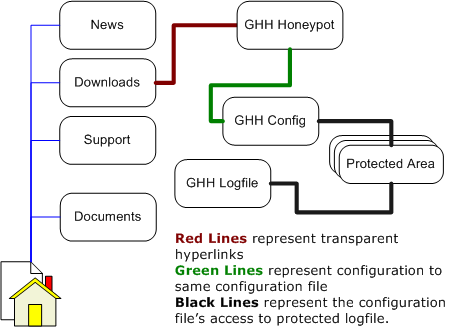
GHH is the reaction to a new type of malicious web traffic: search engine hackers. GHH is a ?Google Hack? honeypot. It is designed to provide reconaissance against attackers that use search engines as a hacking tool against your resources. GHH implements honeypot theory to provide additional security to your web presence.
Google has developed a powerful tool. The search engine that Google has implemented allows for searching on an immense amount of information. The Google index has swelled past 8 billion pages [February 2005] and continues to grow daily. Mirroring the growth of the Google index, the spread of web-based applications such as message boards and remote administrative tools has resulted in an increase in the number of misconfigured and vulnerable web apps available on the Internet.
These insecure tools, when combined with the power of a search engine and index which Google provides, results in a convenient attack vector for malicious users. GHH is a tool to combat this threat.
GHH emulates a vulnerable web application by allowing itself to be indexed by search engines. It's hidden from casual page viewers, but is found through the use of a crawler or search engine. It does this through the use of a transparent link which isn't detected by casual browsing but is found when a search engine crawler indexes a site. The transparent link (when well crafted) will reduce false positives and avoid a fingerprint of the honeypot.
The honeypot connects to a configuration file, and the configuration file writes to a log file which is chosen during configuration. The log file contains information about the host, including IP address, referral information, and user agent.
Using the information gathered in the log file, an administrator can learn more about attackers doing reconnaissance against their site. An administrator can cross reference logs and view a better picture of specific attackers.
GHH can be a minimum of 3 files, including the honeypot, the configuration file, and the log. The transparent link is made into a pre-existing webpage
|
|
#8
|
||||
|
||||
|
cool link but it does seem not to follow all of googles guidelines>_>
|
|
#9
|
|||
|
|||
|
Quote:
|
|
#10
|
|||
|
|||
|
Quote:
Code:
Version {1}

|
 |
«
Previous Thread
|
Next Thread
»
|
|
All times are GMT. The time now is 02:29 PM.





 Linear Mode
Linear Mode

